The Secret Of Info About How To Prevent Syn Attacks
Here are seven key ways to enhance.
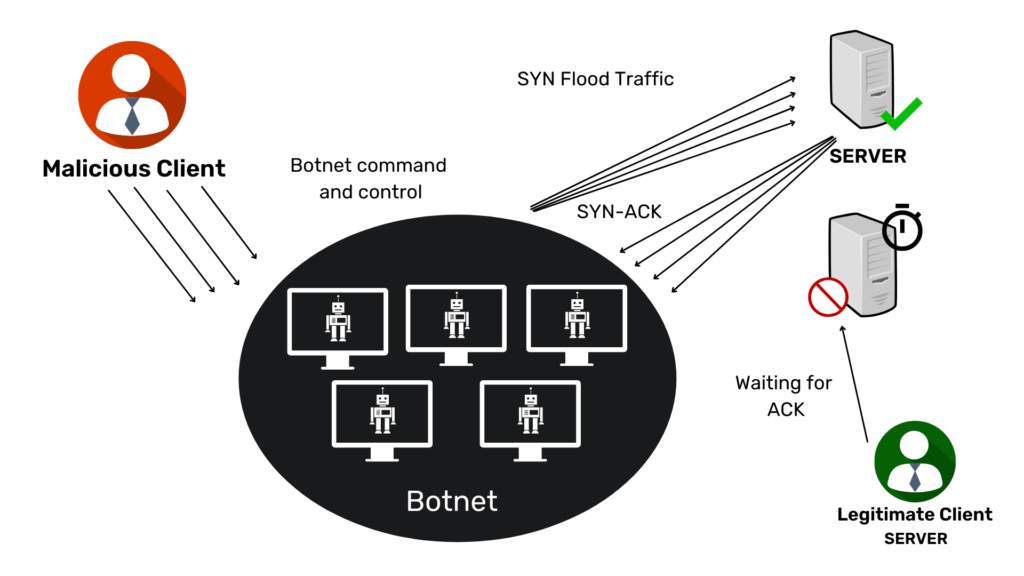
How to prevent syn attacks. Syn cookies are a special type of cookie that is used to. Defining syn flood ddos attacks: The three ways that a syn flood attack can occur are the following:
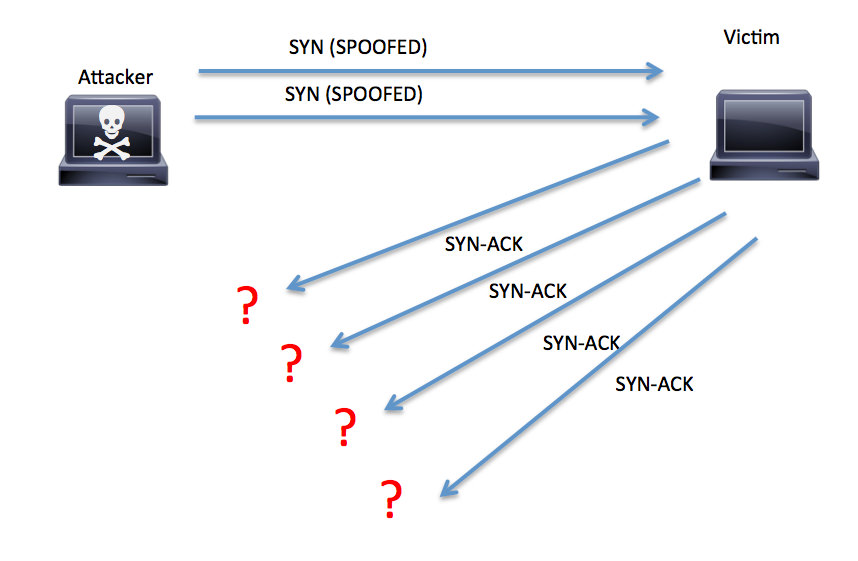
Intrusion detection systems (ids) that can detect and block malicious traffic from a syn flood attack and. Ips devices and firewalls are critical when it comes to network security. A computer starts the conversation from a faked origin point.
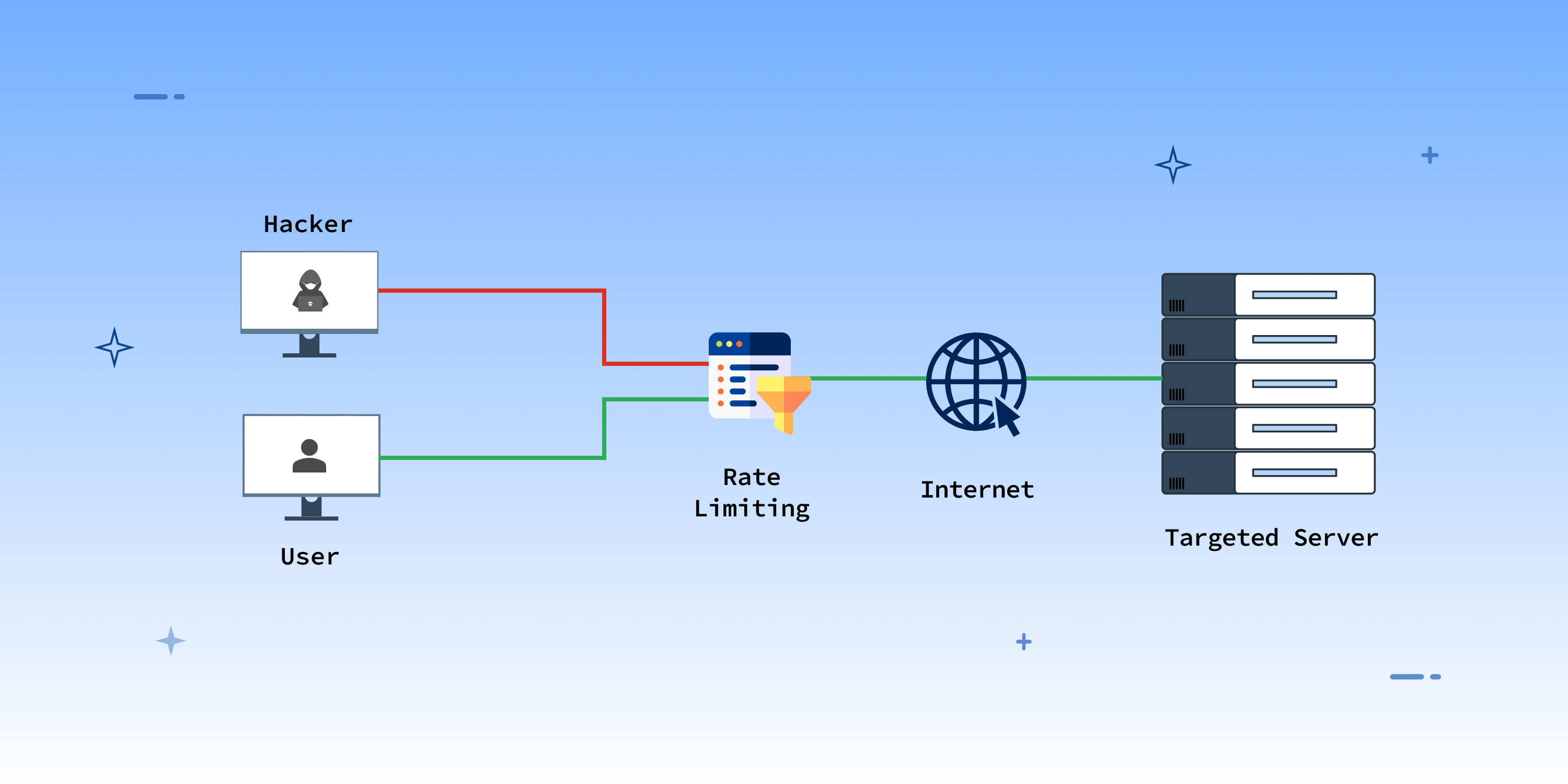
1) first back up your server and registry settings before you begin with any registry edits. Preventing transmission of invalid ip addresses. Configure firewallsto limit incoming traffic and block incoming connections from suspicious or known malicious ip addresses.
Defining syn flood ddos attacks: Asked 11 years, 6 months ago. How to prevent syn flood ddos attacks.
How to protect yourself from a tcp syn flood attack? A denial of service attack’s intent is to deny legitimate users access to a resource such as a network, server etc. Let’s explore what a syn flood attack is, its impact, and preventive measures.
A syn flood attack is. How to prevent a syn flood attack. There are several ways that you can protect your network against a syn flood attack:
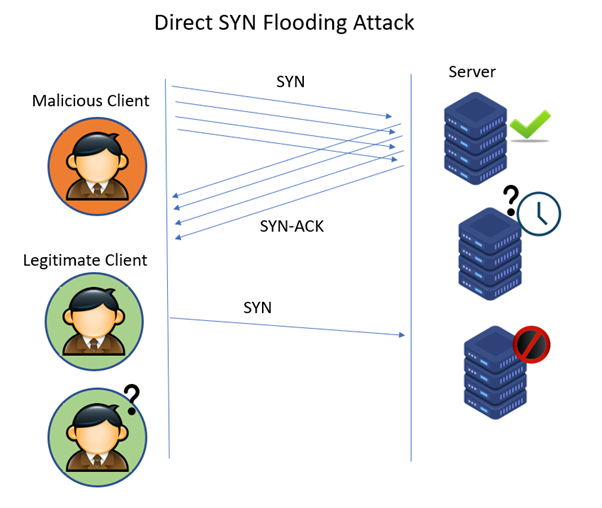
In a spoofed attack, the malicious client spoofs the ip address on each syn packet sent to the. Preventing a network from unwittingly hosting an attack. To protect the network against syn attacks, follow these below steps.
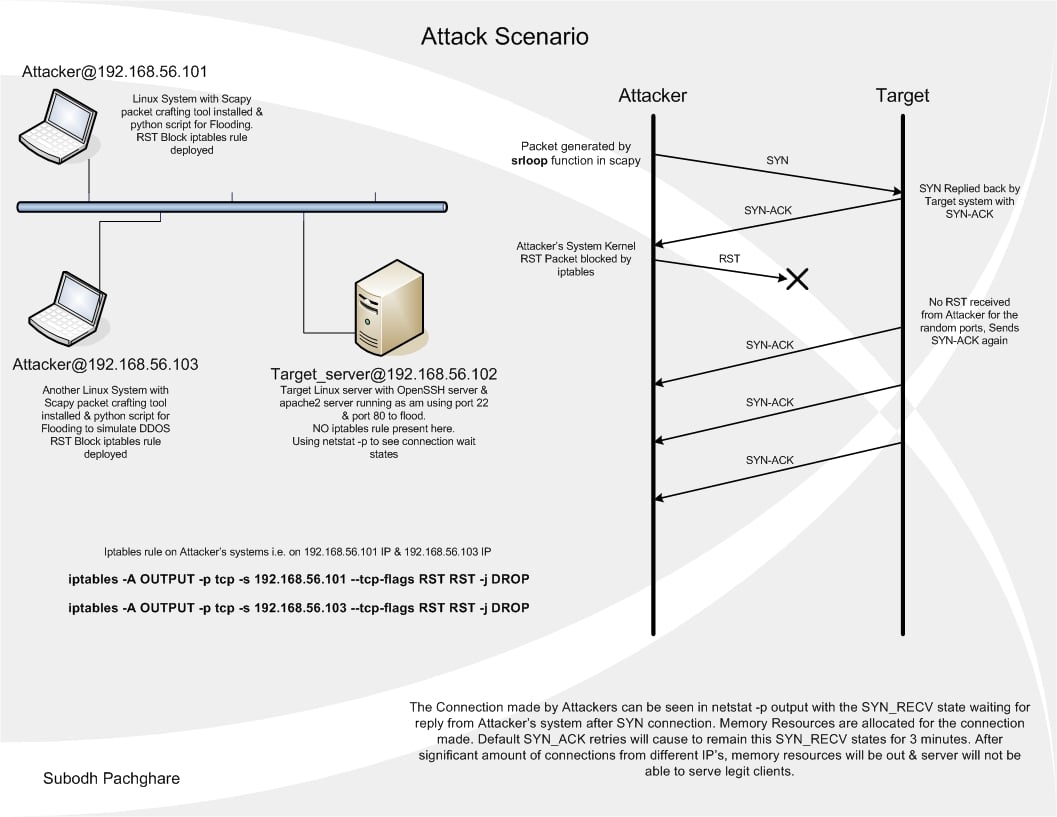
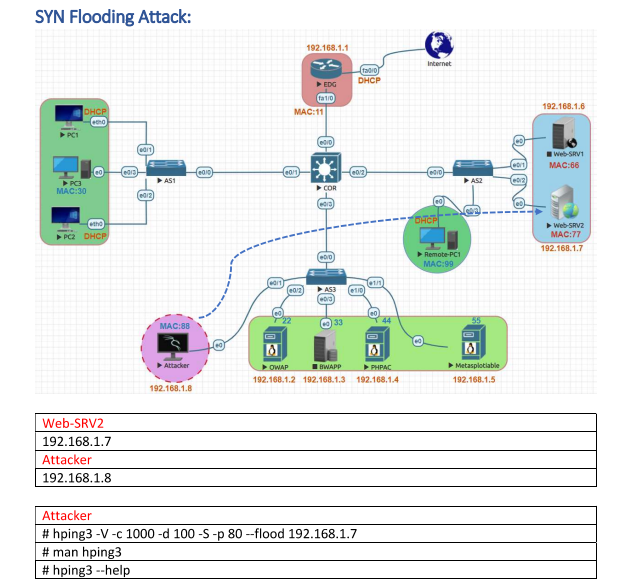
There are two types of attacks, denial of service. Preventing reception of invalid ip addresses. For massive syn flood packets, the key to defending against syn flood attacks is to determine which connection requests come from genuine sources and then.
Common techniques for mitigating syn flood ddos attacks include: How to prevent a syn flood attack. The server's responses go to a computer that didn't request them, and the computer ignores.
You can syn flood attacks by installing an ips, configuring your firewall, installing up to date networking equipment, and installing. However, the issue is that they will fail to offer.